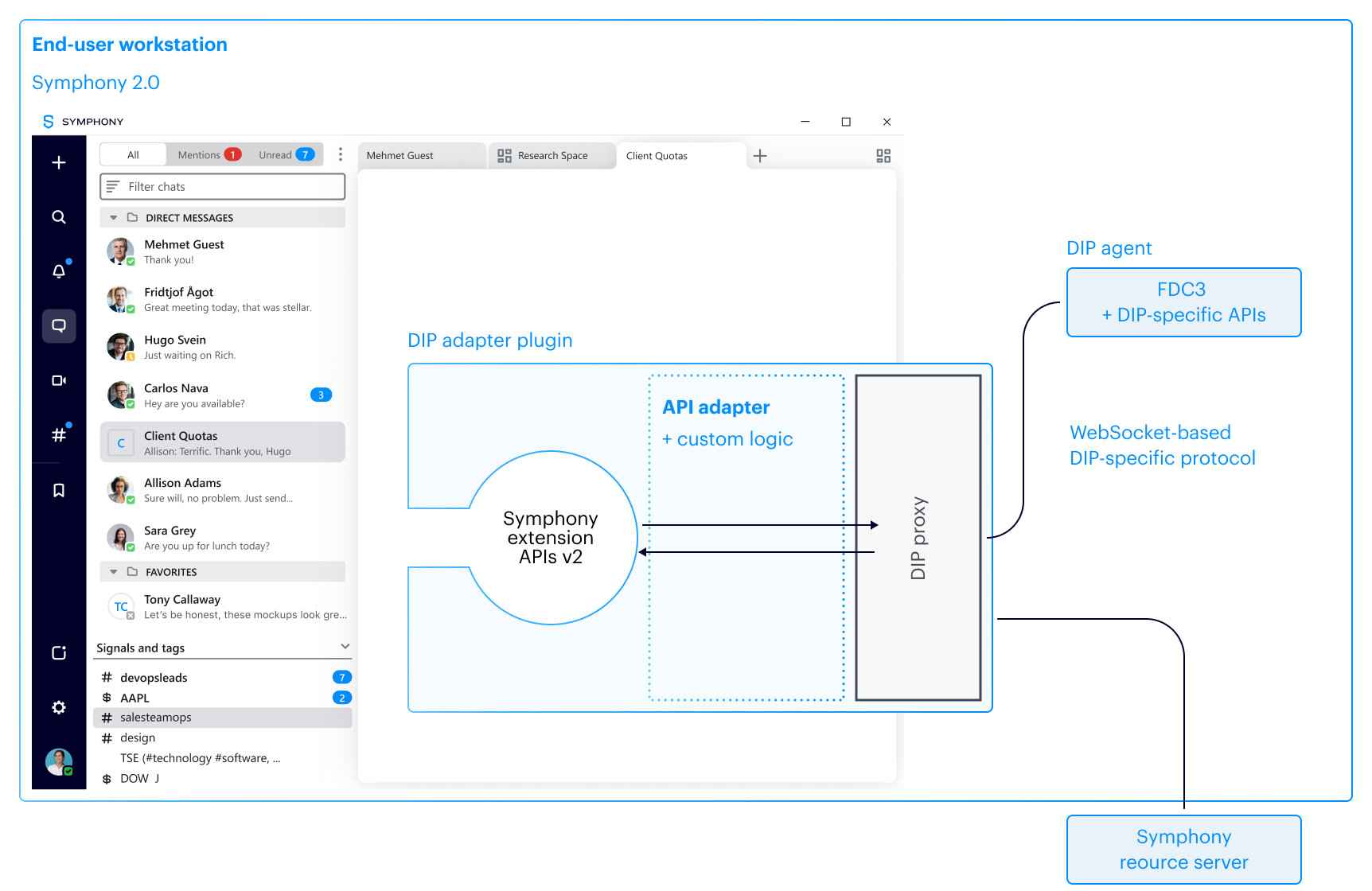
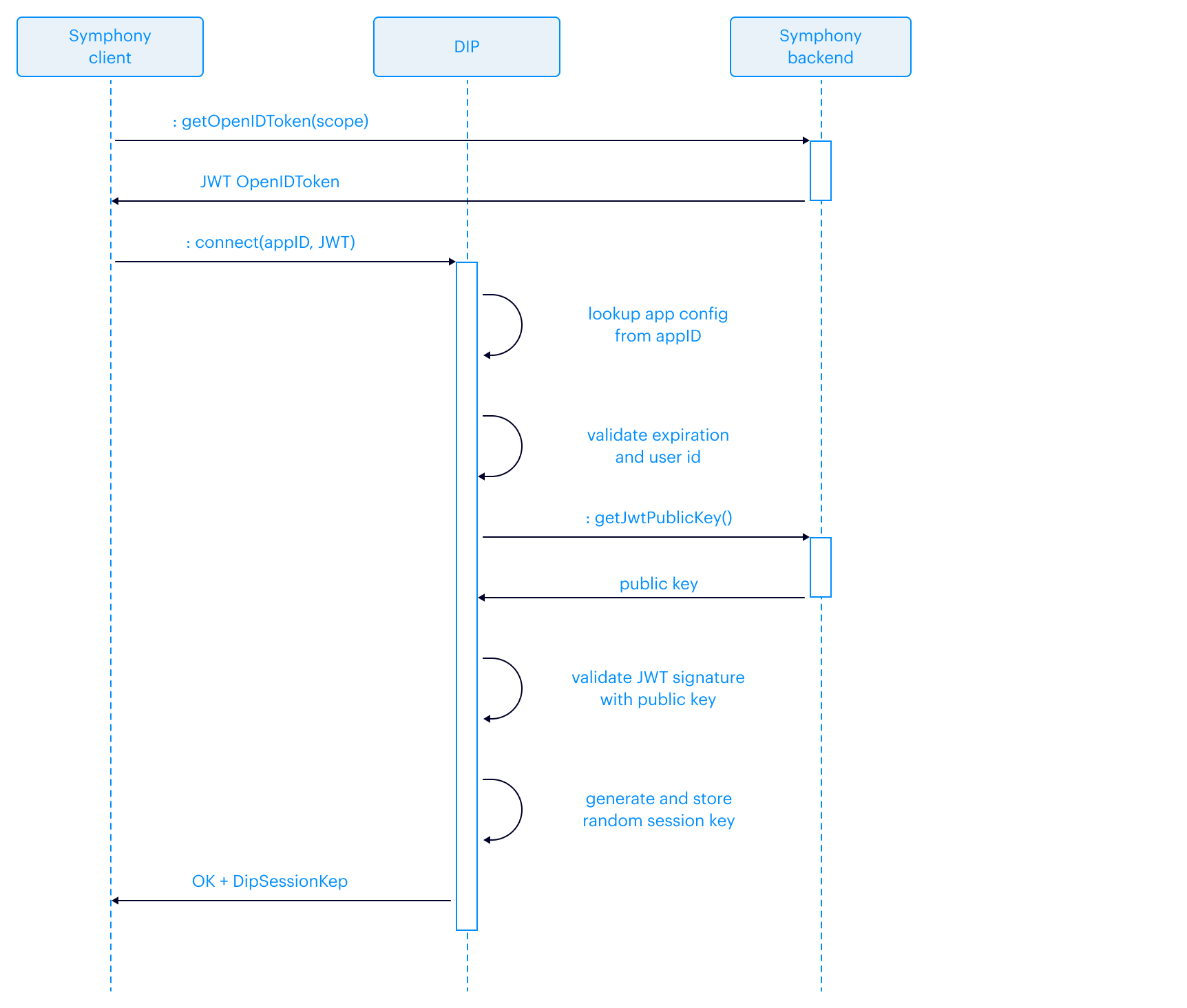
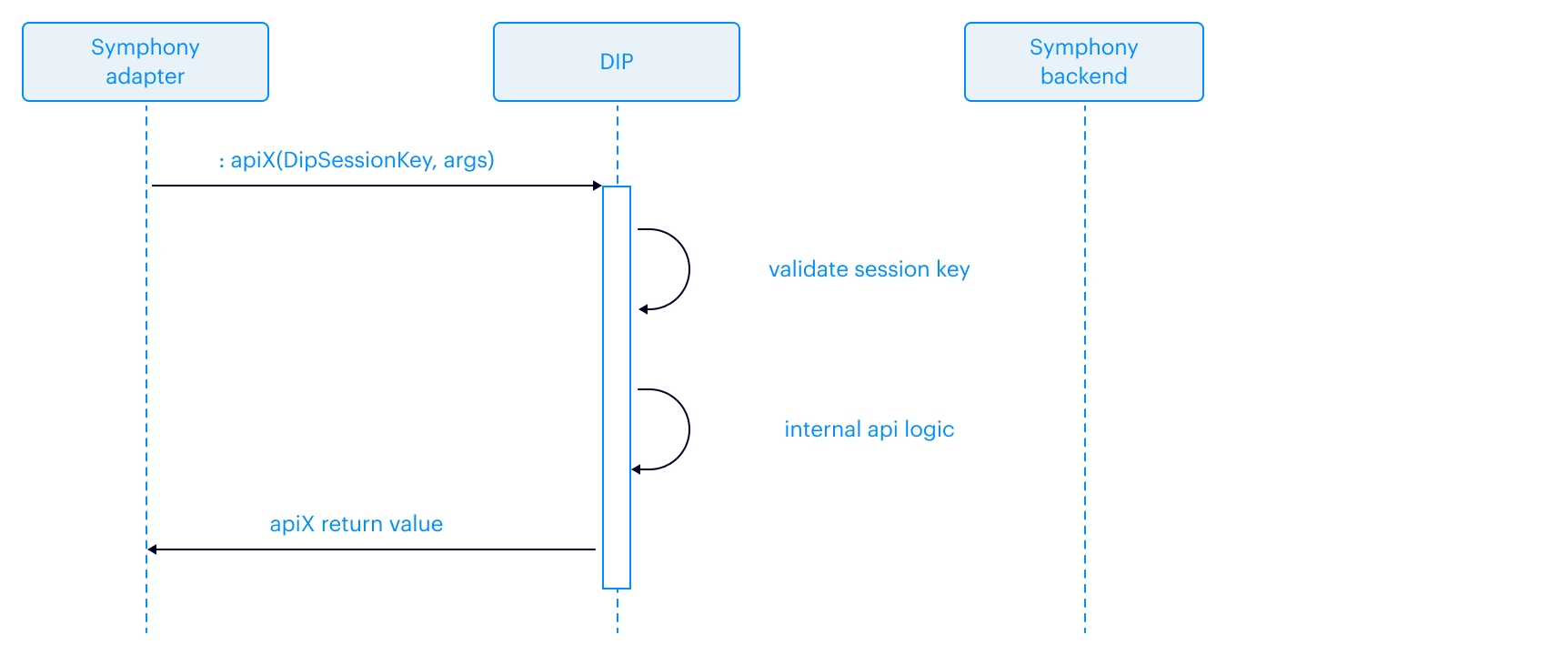
Contemporary Digital Communications: A Review of the Solution Landscape
The current digital environment provides organizations with a range of messaging solutions, each characterized by varying levels of security and compliance capabilities. This has become particularly prominent as people add messaging apps to their personal and professional workflows as a complement to e-mail.